Invoke External Procedures as SQL Functions
Shows the steps to invoke external procedures using PL/SQL within your database.
- External Procedures Overview
External procedures are functions written in a third-generation language and callable from within PL/SQL or SQL as if they were a PL/SQL routine or function. - About Using External Procedures in Autonomous Database
You can invoke and use external procedures in your Autonomous AI Database with user defined functions. - Define the C Procedure
Define the C procedure using one of these prototypes. - Create a Shared Library (.so) File
Create a shared object (.sofile) library. The shared object library contains the C procedure (external procedure) which was defined in the previous step. - Get the OCI Marketplace EXTPROC Stack Application
Shows the steps to get the OCI MarketplaceEXTPROCStack Application. - Launch EXTPROC Stack Application
Launch theEXTPROCStack Application from the EXTPROC Application Details page. - Create Stack for EXTPROC Agent Application
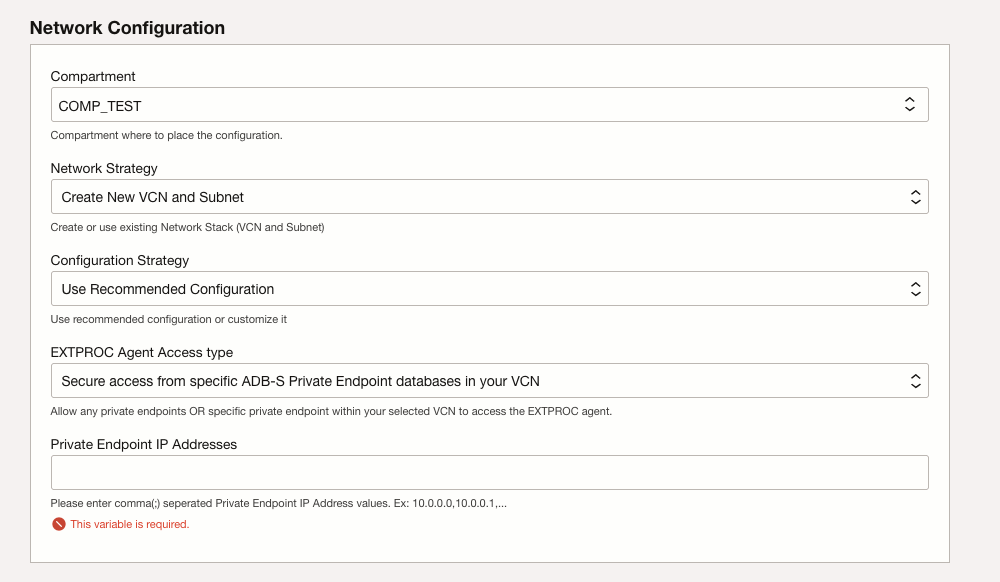
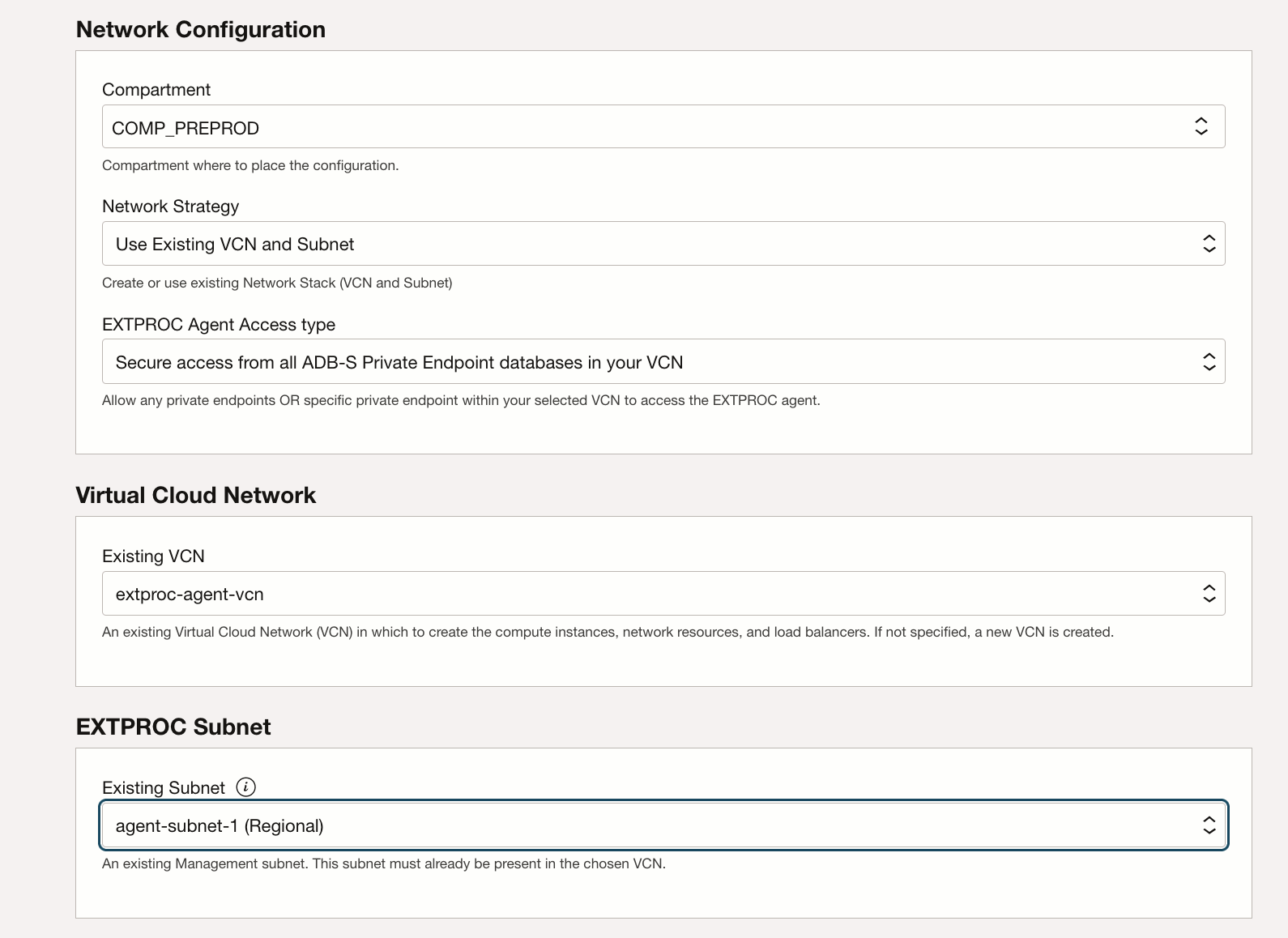
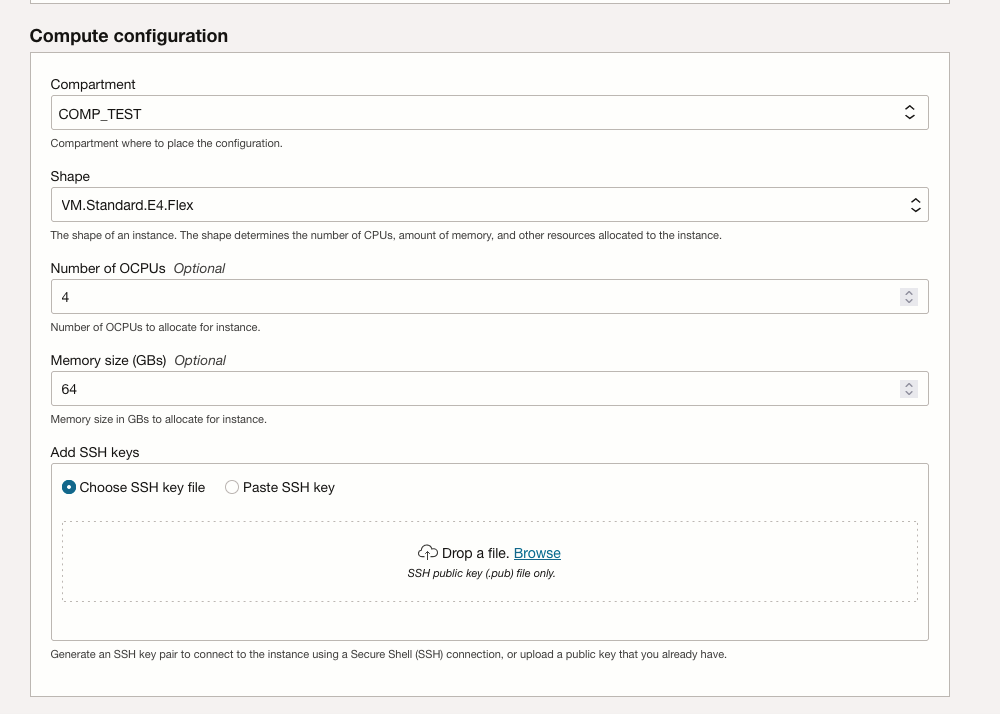
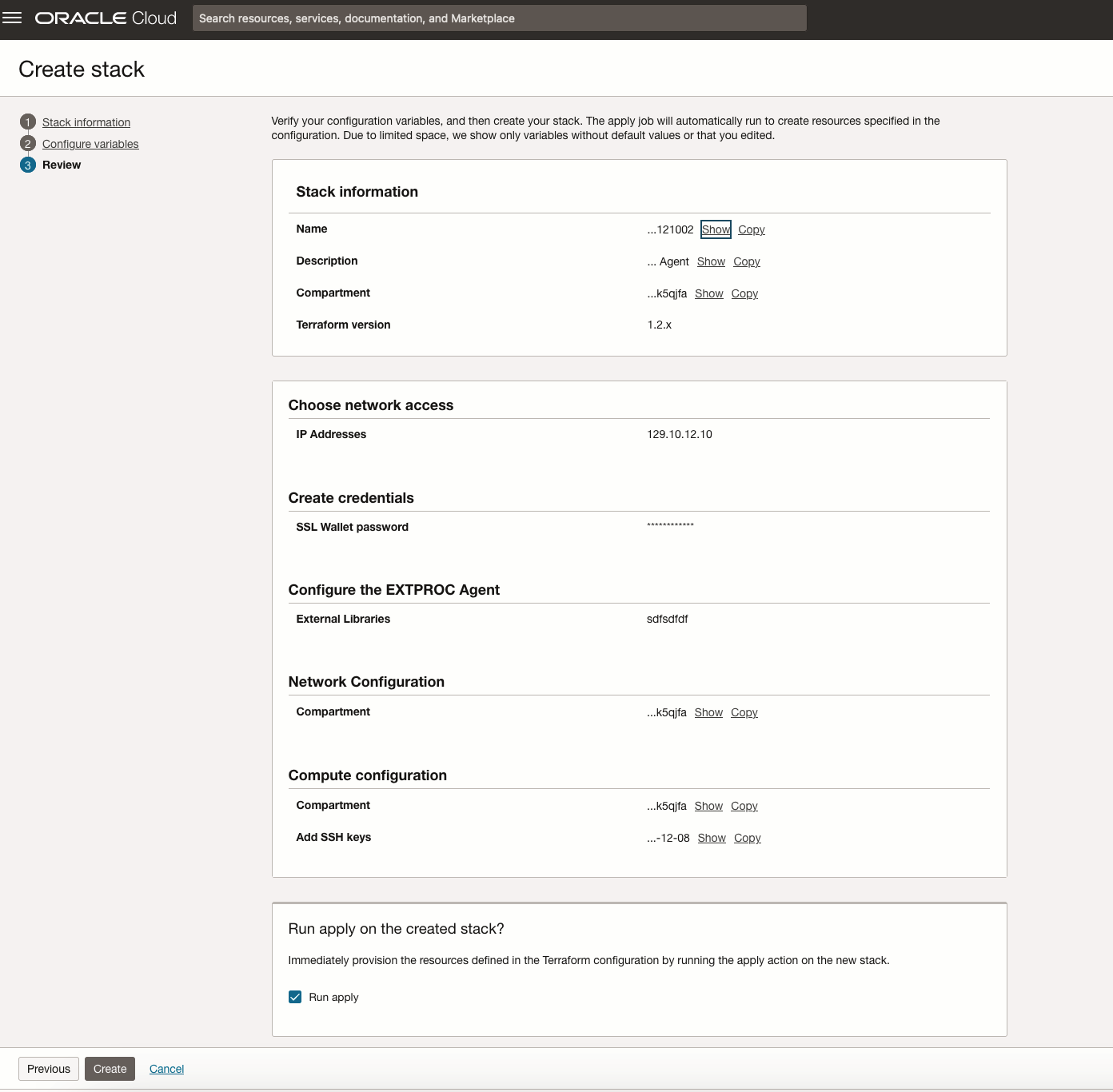
Shows the steps to create Stack forEXTPROCinstance. - Upload Wallet to Create Secure Connection to the EXTPROC Agent Instance
A self-signed wallet is created as part of theEXTPROCagent application creation. This wallet allows you to access theExtrpocagent instance. - Steps to Invoke an External Procedure as a SQL Function
Shows the steps to invoke an external Procedure as a SQL function.
Parent topic: Invoke User Defined Functions
External Procedures Overview
External procedures are functions written in a third-generation language and callable from within PL/SQL or SQL as if they were a PL/SQL routine or function.
External procedures promote reusability, efficiency, and modularity. Existing dynamic link libraries (DLLs) written in other languages can be called from PL/SQL programs. The DLLs are loaded only when needed and they can be enhanced without affecting the calling programs.
Using external procedures also enhances performance, because third-generation languages perform certain tasks more efficiently than PL/SQL, which is better suited for SQL transaction processing.
External procedures are useful when:
-
Solving scientific and engineering problems
-
Analyzing data
-
Controlling real-time devices and processes
See What Is an External Procedure? for more information.
Parent topic: Invoke External Procedures as SQL Functions
About Using External Procedures in Autonomous Database
You can invoke and use external procedures in your Autonomous AI Database with user defined functions.
You do not install external procedures on an Autonomous AI Database instance. To use an external procedure, the procedure is hosted remotely on a VM running in an Oracle Cloud Infrastructure Virtual Cloud Network (VCN).
External procedures are only supported when your Autonomous AI Database is on a private endpoint. The EXTPROC agent instance is hosted on a private subnet and the Autonomous AI Database access the EXTPROC agent through a Reverse Connection Endpoint (RCE).
Autonomous AI Database only supports C language external procedures.
External procedures are deployed by using:
-
An Oracle provided container image with
EXTPROCagent installed and configured as a part of the Oracle Cloud Infrastructure (OCI) Marketplace stack.The
EXTPROCagent instance is hosted remotely on a VM running in an Oracle Cloud Infrastructure Virtual Cloud Network (VCN). The secure communication between your Autonomous AI Database and theEXTPROCagent instance is ensured by setting Network Security Group (NSG) rules such that the traffic is allowed from your Autonomous AI Database instance running on a private endpoint to theEXTPROCagent instance.The
EXTPROCagent image is pre-configured to host and execute external procedures on port 16000. -
PL/SQL procedures to create a library and to register and invoke external functions and procedures.
See DBMS_CLOUD_FUNCTION Package for more information.
Follow these steps to invoke an external procedure on Autonomous AI Database:
-
Define the C procedure. See Define the C Procedure.
-
Create a shared object (
.sofile) library. See Create a Shared Library (.so) File. -
Launch the Autonomous AI Database
EXTPROCstack application. See Get the OCI Marketplace EXTPROC Stack Application. -
Provision and configure Oracle Autonomous AI Database
EXTPROCagent. See Create Stack for EXTPROC Agent Application for more information. -
Configure your Autonomous AI Database to connect to the
EXTPROCagent instance. See Upload Wallet to Create Secure Connection to the EXTPROC Agent Instance for more information. -
Create a remote library using
DBMS_CLOUD_FUNCTION.CREATE_CATALOG. See Steps to Invoke an External Procedure as a SQL Function for more information. -
Use the user defined function you created in the previous step. See Steps to Invoke an External Procedure as a SQL Function for more information.
Parent topic: Invoke External Procedures as SQL Functions
Define the C Procedure
Define the C procedure using one of these prototypes.
-
Kernighan & Ritchie style prototypes. For example:
void UpdateSalary(x) float x; ... -
ISO/ANSI prototypes other than numeric data types that are less than full width (such as
float,short,char). For example:void UpdateSalary(double x) ... -
Other data types that do not change size under default argument promotions.
This example changes size under default argument promotions:
void UpdateSalary(float x) ...
Parent topic: Invoke External Procedures as SQL Functions
Create a Shared Library (.so) File
Create a shared object (.so file) library. The shared object library contains the C procedure (external procedure) which was defined in the previous step.
You generate a shared object library using the following command:
gcc -I/u01/app/oracle/extproc_libs/ -shared -fPIC -o extproc.so UpdateSalary.cThis creates the shared object (.so), extproc.so library. The UpdateSalary procedure, defined in the previous step, is contained in the extproc.so library. The shared object (.so) libraries are dynamically loaded at run time.
Parent topic: Invoke External Procedures as SQL Functions
Get the OCI Marketplace EXTPROC Stack Application
Shows the steps to get the OCI Marketplace EXTPROC Stack Application.
Parent topic: Invoke External Procedures as SQL Functions
Launch EXTPROC Stack Application
Launch the EXTPROC Stack Application from the EXTPROC Application Details page.
This takes you to the Create stack page that allows you to create stack for the EXTPROC agent.
Parent topic: Invoke External Procedures as SQL Functions
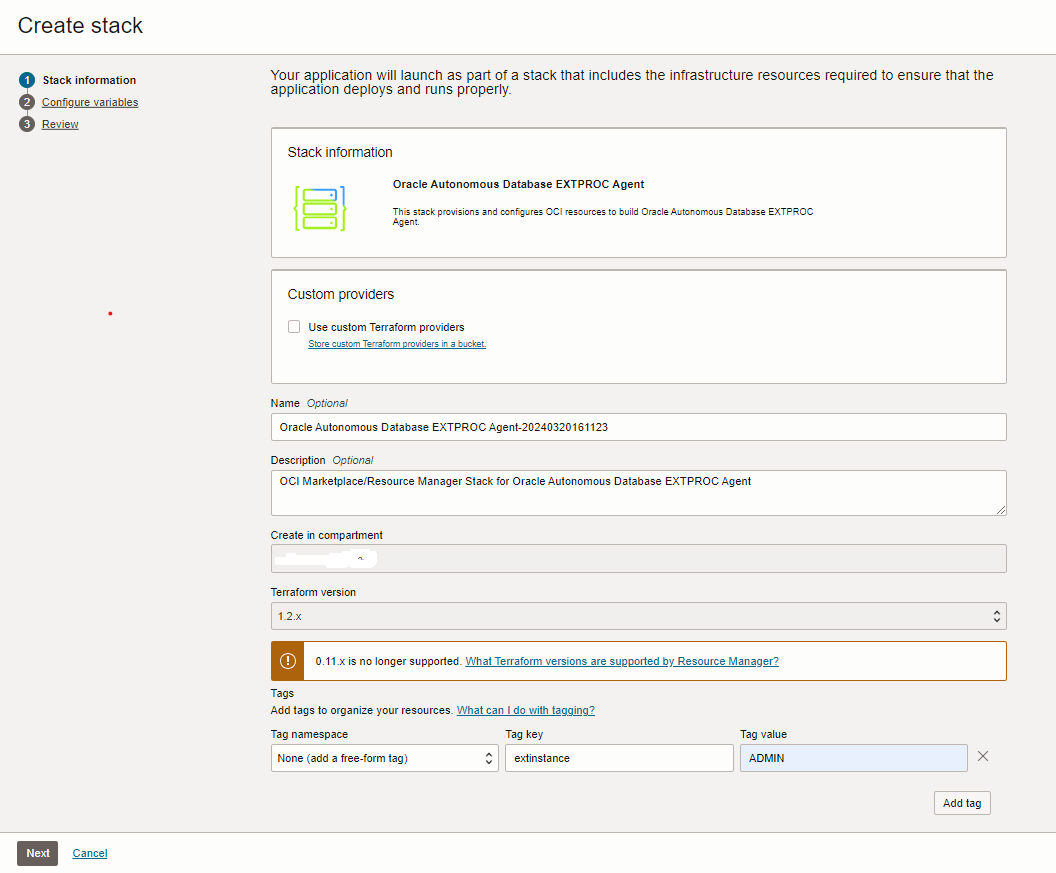
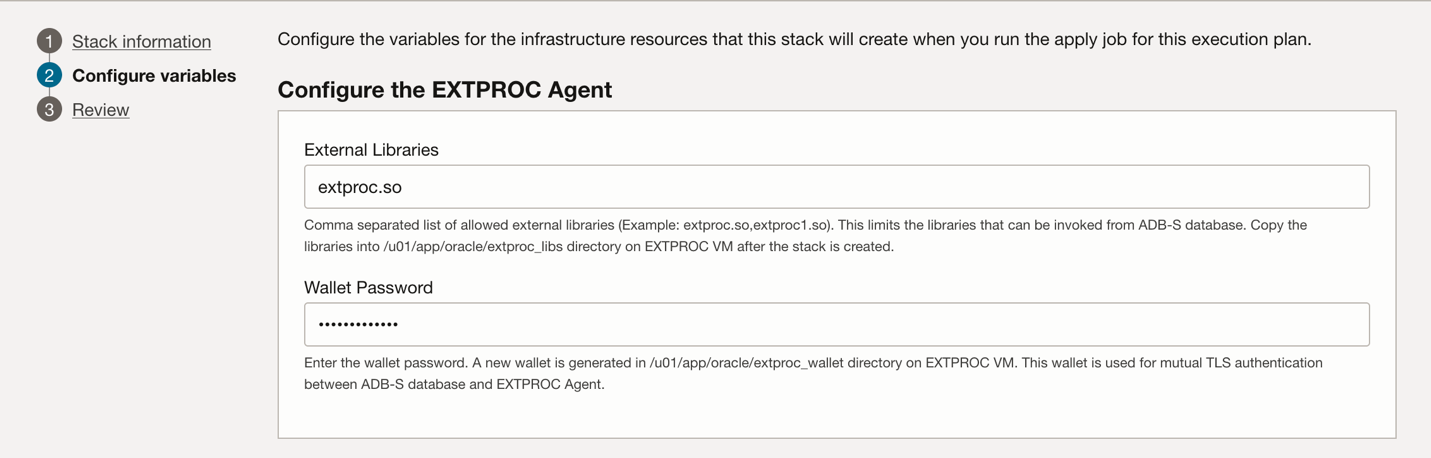
Create Stack for EXTPROC Agent Application
Shows the steps to create Stack for EXTPROC instance.
Parent topic: Invoke External Procedures as SQL Functions
Upload Wallet to Create Secure Connection to the EXTPROC Agent Instance
A self-signed wallet is created as part of the EXTPROC agent application creation. This wallet allows you to access the Extrpoc agent instance.
EXTPROC agent instance, the Autonomous AI Database and the EXTPROC
agent connect using Mutual Transport Layer Security (mTLS). When using Mutual Transport
Layer Security (mTLS), clients connect through a TCPS (Secure TCP) database connection using
standard TLS 1.2 with a trusted client certificate authority (CA) certificate. See About Connecting to an Autonomous AI Database Instance for more information.
You can also obtain and use a public certificate issued by a Certificate Authority (CA).
As a prerequisite, you must export the wallet to Object Storage from the /u01/app/oracle/extproc_wallet directory on the VM where EXTPROC runs.
Follow these steps to upload the wallet to your Autonomous AI Database:
Parent topic: Invoke External Procedures as SQL Functions
Steps to Invoke an External Procedure as a SQL Function
Shows the steps to invoke an external Procedure as a SQL function.
After you launch the OCI Marketplace EXTPROC stack application and configure it to run external procedures, you create a library of SQL wrapper functions that reference and call their respective external procedures.
As a prerequisite, the whitelisted libraries must be copied into the /u01/app/oracle/extproc_libs directory on the EXTPROC VM.
Parent topic: Invoke External Procedures as SQL Functions