Getting Started with OS Management Hub
Get started with OS Management Hub by ensuring service prerequisites are met before enabling the service and registering instances.
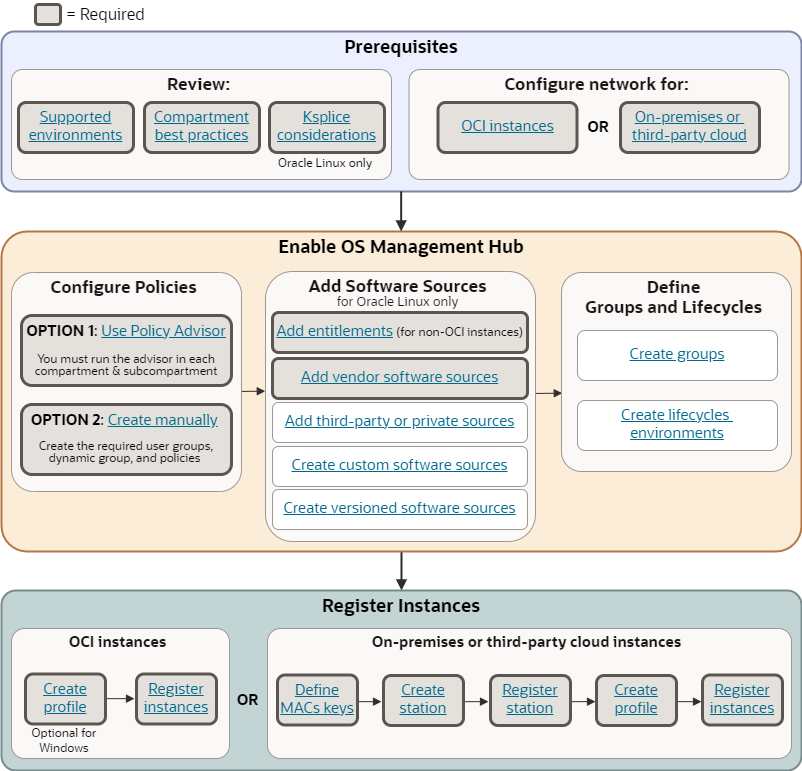
The following diagram provides an overview of getting started with the service. Click an item to view details.
How to Sign In to the Console
To learn how to sign in to the Oracle Cloud Infrastructure Console for the first time, see Sign In to the Console. You can access the Console at https://www.oracle.com/cloud/sign-in.html.
Complete the following to get started:
Review:
- Supported environment
- Compartment best practices
- Ksplice requirements (Oracle Linux instances only)
- Networking requirements
Define policies:
- Option 1: Use the policy advisor
- Option 2: Create manually
Add software sources (for Oracle Linux only):
Register OCI instances:
Register on-premises or third-party cloud instances:
Supported Environments
OS Management Hub is an Oracle Cloud Infrastructure service which can manage OCI instances and on-premises or third-party cloud instances. Verify that the OS version of an instance is supported in the environment you want to manage.
OS Management Hub isn't available on the Oracle Cloud Free Tier instances. If you're using Oracle Cloud Application tenancies, you might not have the required OCI access. Contact your sales representative. Learn more about Oracle's cloud services.
Subscription Requirements
- Oracle Cloud Infrastructure Compute instances (OCI instances) receive Premier Support for free.
-
For on-premises or third-party cloud environments, you must have a valid Oracle Linux Basic or Premier Support subscription to use OS Management Hub.
Supported OS Versions
- OCI instances
-
OS Management Hub is supported on Oracle Linux and Windows platform images for the following OS versions. You can also configure custom images for OS Management Hub by installing the required Oracle Cloud Agent and enabling the OS Management Hub Agent plugin.
-
Oracle Linux 7, 8, or 9
- Windows Server 2016, 2019, or 2022 Standard, Datacenter
Note
OS Management Hub no longer supports Oracle Linux 6. Extended Support for Oracle Linux 6 ended on December 31, 2024. See OS Lifecycle and Support.Important
OS Management Hub requires minimum Oracle Cloud Agent version 1.40. For instances using platform images released before April 2024, upgrade the Oracle Cloud Agent to 1.40 or later. -
- On-premises or third-party cloud instances
-
- Oracle Linux 7, 8, or 9 (x86-64 only)
OS Lifecycle and Support
When an OS reaches the end of its support lifecycle, the OS vendor no longer provides security updates for the OS. Upgrade to the latest version to remain secure. When an OS version reaches the end of its support lifecycle, OS Management Hub:
- No longer provides updates to agents or plugins needed by the service.
- Considers the OS version as unsupported.
- No longer registers instances for unsupported OS versions.
- Might unregister unsupported OS versions and remove resources and references associated with unsupported OS versions.
Additionally, when an OS vendor deprecates or decommissions a software repository, OS Management Hub can no longer provide packages or updates from the repository.
- Oracle Linux
- See Oracle Linux Lifetime Support Policy. Support tiers for an Oracle Linux release include:
- Microsoft Windows
- See Microsoft Windows Server Lifecycle Information.
Supported Third-Party Clouds
OS Management Hub can manage Oracle Linux instances in the following third-party clouds:
- Amazon Web Services (AWS)
- Microsoft Azure
Compartment Considerations
Use compartments to organize and isolate OS Management Hub resources. Follow best practices when allocating resources to particular compartments.
The following resources have compartment restrictions:
- Software sources: Vendor software sources always reside in the root compartment, but can be replicated to other compartments. Custom, versioned, third-party, and private software sources can reside in any compartment.
- Profiles: Service-provided profiles and default profiles always reside in the root compartment. All other profiles can reside in any compartment. See Understanding Profiles.
Best Practices for Compartments
See Learn Best Practices for Setting Up Your Tenancy for general OCI compartment best practices.
For OS Management Hub best practices, when creating groups or lifecycle environments, limit instance members to the same compartment as the group or lifecycle environment. OS Management Hub displays instance members, jobs, and reports for a single compartment at a time. When all instance members are in the same compartment, you have a direct view of all members, jobs, and reports associated with the group or lifecycle environment.
If instance members are in several compartments, your view of instances, jobs, and reports is limited to the selected compartment. You must change the compartment scope when viewing members, examining job logs, and running reports. For example, when looking at a job for a multi-compartment group, you would need to change compartments to view all the associated children jobs. Additionally, depending on your policies, a user might not have permissions to all the compartments for the instance members. These users will have an incomplete view of the group or lifecycle environment.
Moving Resources Between Compartments
You can move most resources between compartments within the same region of your tenancy. However, any scheduled jobs associated with the resource don't move to the destination compartment. They continue to reside in the source compartment. For example, if you move a group, any scheduled jobs associated with the group remain in the old compartment.
Before moving resources, verify that policies and permissions are correctly set so that you don't accidentally lose access to the resource.
To move resources, see:
- Moving a Software Source
- Moving a Profile
- Moving a Management Station
- Moving a Group
- Moving a Lifecycle Environment
- Moving a Scheduled Job
For general information about moving resources between compartments in OCI, see Moving Resources Between Compartments. To move OCI instances, see Moving Compute Resources to a Different Compartment.
Ksplice Considerations (for Oracle Linux only)
For OS Management Hub to apply Ksplice updates, Oracle Linux instances must have access to the Ksplice software sources and the Ksplice client installed.
To use Ksplice, you will need to:
- Add Ksplice software sources to the service. For on-premises or third-party cloud instances, you must also enable an entitlement to use the Ksplice software sources.
- Attach the Ksplice software sources to instances or groups.
- Ensure the correct Ksplice client is installed on the instance.
See Using Ksplice for Oracle Linux for details.
Networking Requirements
Verify your network is configured to support OS Management Hub resources. Networking requirements depend on instance location.
OCI instances
Your OCI virtual cloud network (VCN) must enable communication between your managed instances and the OS Management Hub service. Configure a private subnet with a service gateway that uses the All <region> Services in Oracle Services Network CIDR label. For detailed instructions, see Access to Oracle Services: Service Gateway.
Your instances might require access to the internet. For example, Windows instances that get updates directly from Microsoft, or Oracle Linux instances that use third-party software sources. You can configure internet access for your instances with one of the following:
- A private subnet with a NAT gateway
- A public subnet with an internet gateway
- Microsoft Windows
-
Windows instances get their updates from a Windows update server. You must configure the security list of the instances' subnet to allow instances to access Windows update servers. For more information, see Windows Firewall Rules.
On-premises or supported third-party cloud instances
Your network infrastructure must enable communication to OCI and allow certain traffic between your managed instances and management stations on your internal network.
- Communication to OCI
-
Your network must be able to communicate with OCI. Connectivity can be direct or through an HTTPS proxy. All traffic to API endpoints is cryptographically signed ensuring secure and seamless communication between your network and OCI. The following table lists the minimum required endpoints OS Management Hub requires. For each endpoint, replace
regionwith the customer region identifier. For more information, see Regions and Availability Domains.OS Management Hub Minimum Required Endpoints OS Management Hub Usage osmh.region.oci.oraclecloud.comAccess to the OS Management Hub service. osmh.yum.region.oci.oraclecloud.comAccess to Yum repositories for package management. management-agent.region.oci.oraclecloud.comAccess to the Management Agent Cloud Service (MACS). identity.region.oci.oraclecloud.comauth.region.oci.oraclecloud.comAccess to the Identity and Management (IAM) service for authentication and authorization. objectstorage.region.oraclecloud.comAccess to the latest versions of the OS Management Hub Agent plugin. telemetry-ingestion.region.oraclecloud.comRequired by on premises OS Management Hub clients for telemetry data. Configure your firewall or proxy to allow access to these endpoints on HTTPS port tcp/443. If you're using an HTTPS proxy, you must either:
- Option 1: Ensure the Certificate Authority (CA) that your proxy uses is in the set of trusted authorities on each managed instance and management station.
- Option 2: Configure the proxy for SSL passthrough for the required endpoints.
You can also limit your firewall or proxy rules to the public IP address ranges for services in OCI. See IP Address Ranges for more information.
Note
The minimum required endpoints are for OS Management Hub only. They're not enough for Oracle Cloud Console Access or other OCI services you might use. - Internal Network Communication
-
Your internal network must allow communication between your managed instances and your management stations. When you create a management station, you define several TCP ports for communication between managed instances and management stations. Your internal network must be configured to enable communication between instances and the management station.
- For on-premises, verify your network allows traffic on the proxy and mirror listening ports for your management station.
- For Microsoft Azure, verify that your Azure Virtual Network allows traffic on the proxy and mirror listening ports for your management station.
- For Amazon Web Services (AWS), verify that your Amazon Virtual Private Cloud (VPC) allows traffic on the proxy and mirror listening ports for your management station.
- Oracle Cloud Console Access
-
Access to the Oracle Cloud Console requires a broader range of OCI endpoints and your firewall or proxy must allow access to those endpoints. For more information, see Allowing Access to the Console from Your Network. You can also limit your firewall or proxy rules to the public IP address ranges for services in OCI. See IP Address Ranges for more information.
Third-party and private software sources
If you'll be using third-party or private software sources, ensure that instances can reach the repository URL and GPG key. See Repository URL and GPG Key.
Define IAM Policies
You can configure IAM policies in various ways. The policy advisor provides one way to setup policies quickly within a compartment. If you have specific policy requirements or use cases, see the following for complete information on IAM policy requirements:
Use the policy advisor to quickly enable OS Management Hub for a specific compartment. The advisor defines the necessary user groups, dynamic group, and policies required to use OS Management Hub and Resource Discovery and Monitoring. See What does the policy advisor create?
The policy advisor is only available in OC1.
You must run the policy advisor in each compartment (and child compartment) that you want to use with the service.
-
Verify you have the following permissions. If you only have
readorusepermissions, you'll get an authorization failed error when running the advisor.manage dynamic-groups in tenancymanage groups in tenancymanage policies in tenancy
- Overview.
- Under List Scope, select the compartment you want to use for OS Management Hub.
- Select Run Policy Advisor.
- Review the problems identified with the current policies and groups. Select Next.
- Review the actions the advisor will take. Select Setup.
- Confirm by clicking Setup.
- Rerun the advisor in any other compartments or child compartments that will use the service.
- Add users to the
osmh-adminsandosmh-operatorsgroup. See Managing Groups.
For complete details on the policy advisor, see Using the Policy Advisor.
Management Agent Cloud Service Keys (for non-OCI instances only)
On-premises or third-party cloud instances use the Management Agent Cloud Service (MACS). You must create the Management Agent Cloud Service (MACS) install keys for management stations and instances with OS Management Hub.
You specify the key when registering a management station or instance. The key provides the initial OCI authorization token and determines the compartment of the management station or instance. Create a MACS install key for each compartment that you want manage instances in.
See Understanding the Agent for more information on the OS Management Hub agent.
OCI instances use the Oracle Cloud Agent and don't require a MACS key.
Next steps
- Add vendor software sources to the tenancy.
- For on-premises or third-party cloud, create a management station and use the profile to register the management station as an instance with the OS Management Hub service.
- Create a profile to register an instance with the content associated with specific software sources, a lifecycle environment, or a group.
- Register an instance with the OS Management Hub service.