Kubernetes Using Cloud Shell: Deploy a Java Helidon Application
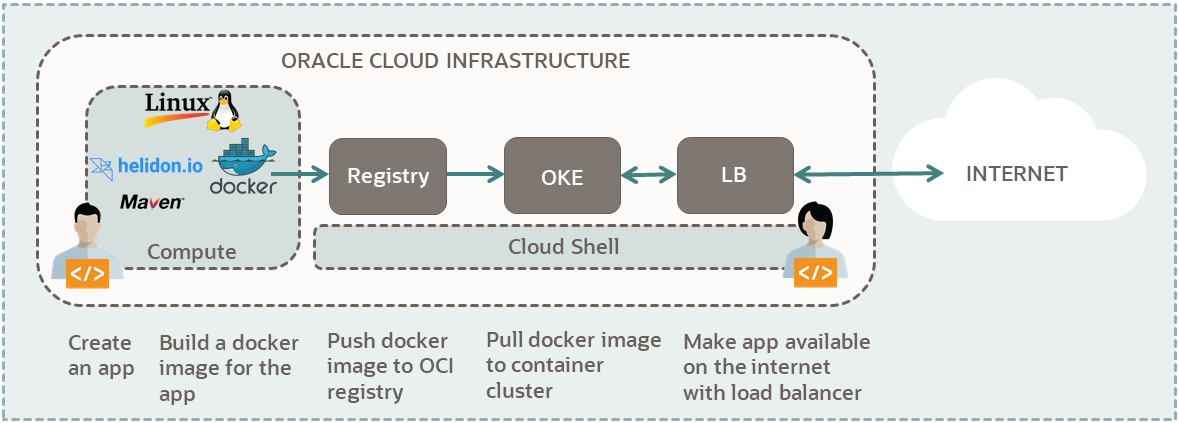
In this tutorial, you use an Oracle Cloud Infrastructure account to set up a Kubernetes cluster. Then, you deploy a Java Helidon application to your cluster using Cloud Shell.
Key tasks include how to:
- Create a Compartment.
- Set up a Kubernetes cluster on OCI.
- Build a Java Helidon application and Docker image.
- Push your image to Container Registry.
- Use Cloud Shell to deploy your Docker application to your cluster.
- Connect to your application from the internet.
For additional information, see:
Before You Begin
To successfully perform this tutorial, you must have the following:
- A paid Oracle Cloud Infrastructure account. See Signing Up for Oracle Cloud Infrastructure.
- Cloud Shell provides the following applications:
- JDK 8+
- Python 3.6.8+
- Kubectl 1.18.10+
- Apache Maven 3.5+
- Docker 19.0.11+
The advantage of using Cloud Shell is all the required tools to manage your application are already installed and ready to use.
1. Prepare
Prepare your environment to create and deploy your application.
- Log in to the Oracle Cloud Infrastructure Console.
- Open the navigation menu, and click Governance and Administration. Under Governance, click Limits, Quotas and Usage.
- Find your service limit for Regions:
- Filter for the following options:
- Service: Regions
- Scope: Tenancy
- Resource: Subscribed region count
- Compartment:
<tenancy-name>(root)
- Find service limit:
- Limit Name:
subscribed-region-count - Service Limit: minimum 2
- Limit Name:
- Filter for the following options:
- Find your available Compute
core count for the VM.Standard.E3.Flex shape:
- Filter for the following options:
- Service: Compute
- Scope:
<first-availability-domain>. Example:EMlr:US-ASHBURN-AD-1 - Resource: Cores for Standard.E3.Flex and BM.Standard.E3.128 Instances
- Compartment:
<tenancy-name>(root)
- Find available core count:
- Limit Name:
standard-e3-core-ad-count - Available: minimum 1
- Limit Name:
- Repeat for Scope:
<second-availability-domain>and<third-availability-domain>. Each region must have at least one core available for this shape.
- Filter for the following options:
- Find out if you have 50 GB of Block Volume available:
- Filter for the following options:
- Service: Block Volume
- Scope:
<first-availability-domain>. Example:EMlr:US-ASHBURN-AD-1 - Resource Volume Size (GB)
- Compartment:
<tenancy-name>(root)
- Find available core count:
- Limit Name:
total-storage-gb - Available: minimum 50
- Limit Name:
- Repeat for Scope:
<second-availability-domain>and<third-availability-domain>. Each region must have at least 50 GB of block volume available.
- Filter for the following options:
- Find out how many Flexible Load Balancers you have available:
- Filter for the following options:
- Service: LbaaS
- Scope:
<your-region>. Example:us-ashburn-1 - Resource:
<blank> - Compartment:
<tenancy-name>(root)
- Find the count for the following shapes
- Limit Name:
lb-flexible-bandwidth-count - Available: minimum 1
- Limit Name:
- Filter for the following options:
This tutorial creates three compute instances with a VM.Standard.E2.1 shape for the cluster nodes. To use another shape, filter for its core count. For example, for VM.Standard2.4, filter for Cores for Standard2 based VM and BM Instances and get the count.
For a list of all shapes, see VM Standard Shapes.
This tutorial creates three compute instances with a VM.Standard.E3.Flex shape for the cluster nodes. To use another shape, filter for its core count. For example, for VM.Standard2.4, filter for Cores for Standard2 based VM and BM Instances and get the count.
For a list of all shapes, see VM Standard Shapes.
This tutorial uses a 'Quick Create' workflow to create a cluster with a public regional subnet that hosts a flexible load balancer. To use a different load balancer, you can use a custom workflow to explicitly specify which existing network resources to use, including the existing subnets in which to create the load balancers.
To use another bandwidth for the load balancer, filter for its count, for example 100-Mbps bandwidth or 400-Mbps bandwidth.
- In the Console's top navigation bar, click the Profile menu (your avatar).
- Click your username.
- Click Auth Tokens.
- Click Generate Token.
- Give it a description.
- Click Generate Token.
- Copy the token and save it.
- Click Close.
Ensure that you save your token right after you create it. You have no access to it later.
2. Set Up a Cluster
Install and configure management options for your Kubernetes cluster. Later, deploy your application to this cluster.
If your username is in the Administrators group, then skip this section. Otherwise, have your administrator add the following policy to your tenancy:
allow group <the-group-your-username-belongs> to manage compartments in tenancyWith this privilege, you can create a compartment for all the resources in your tutorial.
- In the Console's top navigation bar, open the Profile menu (your avatar).
- Click your username.
- In the left pane, click Groups.
- In a notepad, copy the Group Name that your username belongs.
- Open the navigation menu and click Identity & Security. Under Identity, click Policies.
- Click Create Policy.
- Fill in the following information:
- Name:
manage-compartments - Description:
Allow the group <the-group-your-username-belongs> to list, create, update, delete and recover compartments in the tenancy. - Compartment:
<your-tenancy>(root)
- Name:
- For Policy Builder, click Show manual editor.
- Paste in the following
policy:
allow group <the-group-your-username-belongs> to manage compartments in tenancy - Click Create.
Reference
The compartments resource-type in Verbs + Resource-Type Combinations for IAM
Create a compartment for the resources that you create in this tutorial.
- Log in to the Oracle Cloud Infrastructure Console.
- Open the navigation menu and click Identity & Security. Under Identity, click Compartments.
- Click Create Compartment.
- Fill in the following information:
- Name:
<your-compartment-name> - Description:
Compartment for <your-description>. - Parent Compartment:
<your-tenancy>(root)
- Name:
- Click Create Compartment.
Reference: Create a compartment
If your username is in the Administrators group, then skip this section. Otherwise, have your administrator add the following policy to your tenancy:
allow group <the-group-your-username-belongs> to manage all-resources in compartment <your-compartment-name>With this privilege, you can manage all the resources in your compartment, essentially giving you administrative rights in that compartment.
- Open the navigation menu and click Identity & Security. Under Identity, click Policies.
- Select your compartment from the Compartment list.
- Click Create Policy.
- Fill in the following information:
- Name:
manage-<your-compartment-name>-resources - Description:
Allow users to list, create, update, and delete resources in <your-compartment-name>. - Compartment:
<your-tenancy>(root)
- Name:
- For Policy Builder, select the following choices:
- Policy use cases:
Compartment Management - Common policy templates:
Let compartment admins manage the compartment - Groups:
<the-group-your-username-belongs> - Location:
<your-tenancy>(root)
- Policy use cases:
- Click Create.
Reference
Create a cluster with default settings and new network resources through the 'Quick Create' workflow.
After you create a Kubernetes cluster, set up Cloud Shell to access the cluster.
With your cluster access setup, you are now ready to prepare your application for deployment.
3. Build your Docker Application
Next, set up Helidon MP on Cloud Shell. Then, create and run a Helidon application.
Create your Java Helidon application.
You have successfully built the Helidon application.
Run your Java Helidon application.
You have successfully created a Hello World application using the Helidon MicroProfile service on Oracle Cloud Shell.
References:
- For detailed information on this example, see Helidon MP Quick Start.
- To create your own application, see Helidon MP Config Guide.
Next, create a Docker image for your Helidon application.
4. Deploy Your Docker Image
With your Helidon image created, now you can deploy it.
With your local Docker image created, push the image to the Container Registry.
Follow these steps.
Find your image in Container Registry after the push command is complete.
What's Next
You have successfully created a Helidon MicroProfile Hello World application, deployed it to a Kubernetes cluster, and accessed the app from the internet.
Check out these sites to explore more information about development with Oracle products: