Cross-Tenancy Policies
Your organization may want to access resources in other tenancies, or it may want to share resources with another organization that has its own tenancy. The other organization could be another business unit in your company, a customer of your company, a company that provides services to your company, and so on. In such cases, you need cross-tenancy policies in addition to the normally required policies.
To access and share resources, the administrators of both tenancies need to create special cross-tenancy policy statements that explicitly state the resources that can be accessed and shared. These special statements use the words Endorse, Admit, and Define.
Endorse, Admit, and Define Statements
An overview of the special verbs used in cross-tenancy statements:
- Endorse: States the general set of abilities that a group in your own tenancy can perform in other tenancies. The Endorse statement always belongs in the tenancy that contains the group of users crossing the boundaries into the other tenancy to work with that tenancy's resources. In the examples, we refer to this tenancy as the group tenancy.
- Admit: States the kind of ability in your own tenancy that you want to grant a group from the other tenancy. The Admit statement belongs in the tenancy who is granting "admittance" to the tenancy. The Admit statement identifies the group of users that requires resource access from the group tenancy and is identified with a corresponding Endorse statement. In the examples, we refer to this tenancy as the resource tenancy.
-
Define: Assigns an alias to a tenancy OCID for Endorse and Admit policy statements. A Define statement is also required in the resource tenancy to assign an alias to the IAM group OCID from the group tenancy for Admit statements. The alias is a friendly name of your choosing. You do not have to use the real display name of the tenancy or group.
Include a Define statement in the same policy entity as the Endorse or Admit statement.
The Endorse and Admit statements work together. An Endorse statement resides in the group tenancy while an Admit statement resides in the resource tenancy. Without a corresponding statement that specifies access, a particular Endorse or Admit statement grants no access. Both tenancies must agree on access.
You must define cross-tenancy statements in the root compartment of the tenancy, not in any child compartment.
To illustrate, here's an example of one possible cross-tenancy configuration. The resources (connections, secrets, and private endpoints) are in a different tenancy than the group that should have access to them.
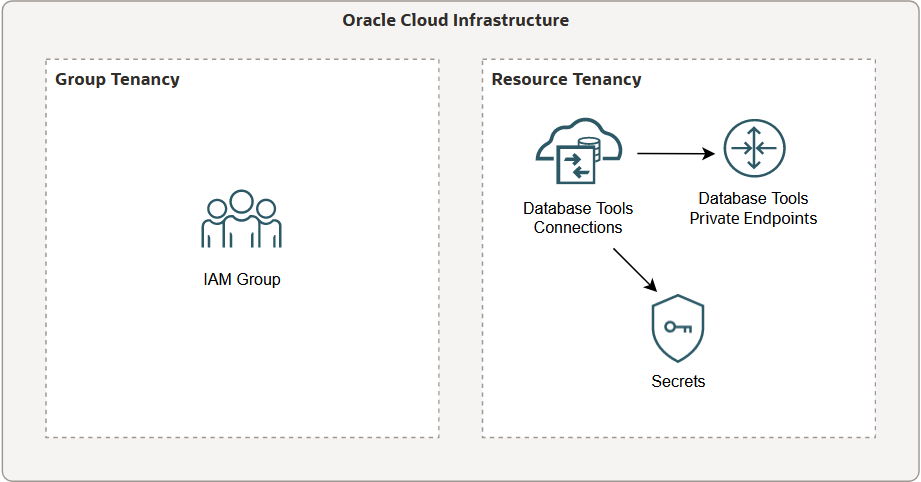
Group Tenancy Policy Statements
As the group tenancy administrator, you create policy statements that:
- Define an alias for the resource tenancy. The resource tenancy administrator must provide the OCID of the resource tenancy.
- Endorse an IAM group in your tenancy to access resources in the resource tenancy.
The following is an example of a broad policy statement that endorses an IAM
group in your tenancy called DatabaseToolsAdministrators to do anything
with all Database Tools resources in any tenancy:
Endorse group DatabaseToolsAdministrators to manage database-tools-family in any-tenancyTo write a policy that reduces the scope from all tenancies to a single
resource tenancy, you must reference the resource tenancy OCID provided by the resource
tenancy administrator. The following is an example of policy statements that endorse the
group DatabaseToolsAdministrators to manage Database Tools resources in
a tenancy referred to as ResourceTenancy:
Define tenancy ResourceTenancy as <resource_tenancy_ocid>
Endorse group DatabaseToolsAdministrators to manage database-tools-family in tenancy ResourceTenancy
You should only endorse the group to have the minimum required permissions.
The following is an example of policy statements that only endorse the IAM group
DatabaseToolsConnectionUsers to use Database Tools connections and
read secrets in ResourceTenancy:
Define tenancy ResourceTenancy as <resource_tenancy_ocid>
Endorse group DatabaseToolsConnectionUsers to use database-tools-connections in tenancy ResourceTenancy
Endorse group DatabaseToolsConnectionUsers to read secret-family in tenancy ResourceTenancyResource Tenancy Policy Statements
As the resource tenancy administrator, you create policy statements that:
- Define aliases for the group tenancy and the IAM group that is allowed to access resources in your tenancy. The group tenancy administrator must provide the OCIDs of the group tenancy and group.
- Admit the group from the group tenancy to access Database Tools resources that you want to allow access to in your tenancy.
The following is an example of policy statements that admit the IAM group
DatabaseToolsAdministrators from a group tenancy referred to as
GroupTenancy to do anything with all Database Tools resources in
your tenancy:
Define tenancy GroupTenancy as <group_tenancy_ocid>
Define group DatabaseToolsAdministrators as <database_tools_administrators_group_ocid>
Admit group DatabaseToolsAdministrators of tenancy GroupTenancy to
manage database-tools-family in tenancy
You can restrict the group's access to a specific compartment in your
tenancy. The following is an example of policy statements that admit
DatabaseToolsAdministrators to do anything with all Database Tools
resources only in the SharedConnections compartment in your
tenancy:
Define tenancy GroupTenancy as <group_tenancy_ocid>
Define group DatabaseToolsAdministrators as <database_tools_administrators_group_ocid>
Admit group DatabaseToolsAdministrators of tenancy GroupTenancy to
manage database-tools-family in compartment SharedResourcesYou should only admit the group to have the minimum required permissions. The
following is an example of policy statements that only admit an IAM group called
DatabaseToolsConnectionUsers to use Database Tools connections and
read secrets in the SharedConnections compartment in your tenancy:
Define tenancy GroupTenancy as <group_tenancy_ocid>
Define group DatabaseToolsConnectionUsers as <database_tools_connection_users_group_ocid>
Admit group DatabaseToolsConnectionUsers of tenancy GroupTenancy to use database-tools-connections in compartment SharedResources
Admit group DatabaseToolsConnectionUsers of tenancy GroupTenancy to read secret-family in compartment SharedResources